This article summarizes the webinar ‘Is Your Mobile App Secure’, presented by Irene Brime, Managing Director and Co-founder of SHIELD, and hosted by Zartis under the webinar series Ecommerce: Behind The Tech Scene. You can watch the full webinar session on mobile app security here.
In this blog post, we will first look at the various tools and techniques used in fraud attacks. Then, we will look into different scenarios and how you can prevent such attacks from happening.
Mobile App Security
There’s a new war being waged – and it’s happening on your smartphone. The technology landscape has changed tremendously in the last few years, with many online fraudsters shifting their attention from websites to mobile apps.
There are two main reasons for this. The first is that there is a false yet persistent perception that mobile apps are inherently secure. The second is that these days, individual apps are trying to offer just about everything. In an increasingly digitised world, convenience is king, which has led to the rise of the ‘superapp’ – apps that house several services under one roof.
Uber is a typical example. Although it started out as a ride hailing company, it soon began offering services such as online payments, food delivery, and e-bike rentals, to name just a few. This decision helped propel it to app stratosphere – it’s now a household name and boasts over 75 million users. But every rose has its thorn. The wider an app’s attack surface, the harder it is to secure, and if an account is breached, the damage can be devastating.
Fraudsters today will attack all and any products and features, which makes it vital that the fraud, risk and mobile security teams look at their ecosystem and determine where their vulnerabilities lie.
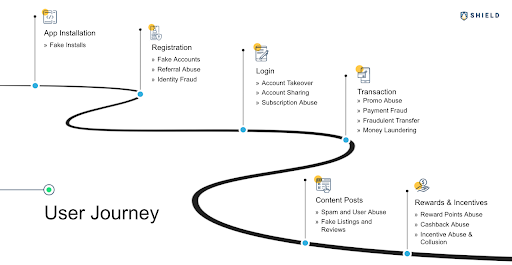
Understanding the User Journey
Incidentally, almost every part of the user journey is vulnerable. Typically, a user journey begins by logging in to an app and ends with completing one or more actions, such as making a payment, booking a ride, redeeming loyalty points, or accessing a loyalty card. Although fraud attacks used to be more common at the payment checkpoint, fraud today can happen at any of them. To mitigate the vulnerabilities in their mobile app security, businesses must protect every single checkpoint as well as understand the various fraud attacks that can happen at each.
Common Fraud Tools and Techniques
It’s never been easier to commit fraud. With most fraud tools only a quick google search away, fraudsters and fraud attacks have increased significantly in recent years. The most common tools and techniques used for fraud can be grouped into four main categories:
 1. App Cloners
1. App Cloners
App cloners allow users to create clones or duplicate an installed app on a mobile phone. By using an app cloner, fraudsters are able to create and access multiple instances of the same app from a single device. This makes it very easy to create multiple fake accounts and significantly reduces the cost of committing fraud.
 2. VPN Apps
2. VPN Apps
 3. GPS Spoofers
3. GPS Spoofers
GPS spoofers differ from VPNs apps in that they change a device’s geolocation without altering the IP address. They are commonly used to commit ride-hailing fraud, where a local driver will use a GPS spoofer to plant their location in a lucrative area – despite not physically being there yet. This enables them to accept better-paying rides and avoid queues by the time they do arrive in the area.
4. Emulators
Emulators simulate mobile devices on a desktop environment. Although they don’t change a device’s base functionalities, emulators make it easier and faster to install malicious tools and carry out automated attacks.
Common Fraud Scenarios
1. Account Takeovers (by Brute-Forcing)
A large number of fraud attacks start with an account takeover. By breaking into a genuine account, fraudsters can masquerade as a good user until the moment they commit fraud. To take over an account, fraudsters typically use a number of password-cracking techniques combined with the tools mentioned above to try and brute-force their way in.
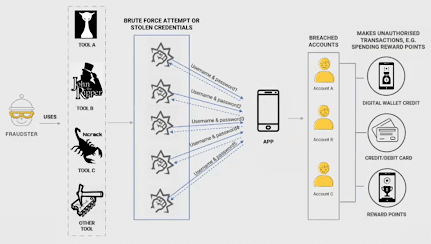
Once the account is breached, fraudsters will have access to any services offered to a user, such as credit cards, digital wallets, and reward points. Mitigating brute-force attempts involves maintaining good cyber hygiene practices, such as having strong passwords and multi-factor authentication protocols in place.
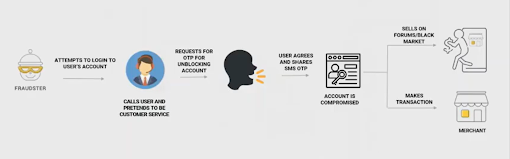
2. Account Takeovers (by Social Engineering)
Fraudsters have also been known to take over accounts by way of social engineering, which involves using psychological manipulation to trick users into making security mistakes or giving away sensitive information. A classic example is the fake customer service agent asking someone to reveal their password over the phone.
3. Fake Account Registration
Fake accounts are often used in combination with stolen credit card credentials to make unauthorized purchases, abuse promotions, and take advantage of incentives given to good users.
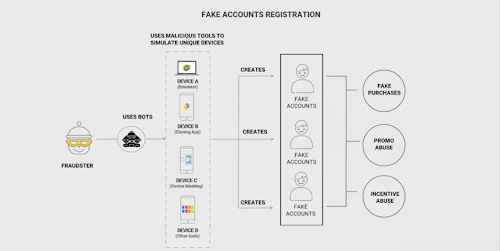
Fraudsters will often use bots when creating fake accounts as they allow them to create multiple accounts with minimal effort. In addition, fraudsters will use VPNs, GPS spoofers, and emulators to make each account look like it comes from a unique device.
4. Referral Abuse
Referral abuse is extremely common, and something that even good users are tempted to do now and again. For example, one of Latin America’s largest ride-hailing companies began its growth journey by offering monetary incentives to any users that referred a friend. This incentive was taken advantage of by fraudsters who would use the malicious tools mentioned above to create fake accounts and refer the app to themselves, thus reaping their own rewards.
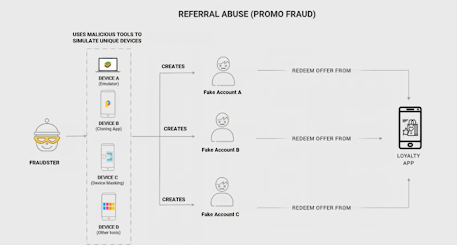
Although fraud is typically associated with making unauthorized payments, referral and incentive abuse can also cause serious financial damage. Understanding that fraud can happen in many ways will result in businesses being better protected and better prepared.
5. Fraudulent Credit Card Payments
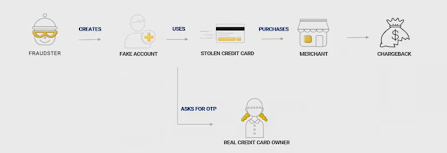
Last but not least, credit card fraud often involves using a fake account and stolen credit card details to make a purchase. Once made, the true owner of the credit card would ask for a refund for an unauthorized purchase, and the merchant loses out.
How Can I Prevent Fraud Attacks?
All of the attacks mentioned above are similar in that they mimic the behavior of real users, and use a range of malicious tools to do so. A sure-fire way of preventing any of these attacks from happening is by leveraging a device’s fingerprint to detect whether any malicious activity is taking place.
A device fingerprint is information (or intelligence) collected about the software and hardware of a device for the purpose of identification. Examples of this information include a device’s operating system, battery level, or IP address. Given that each device is associated with a specific user account, when enough information about a device is changed, or the device fingerprint shows signs of risky behavior, it’s worth investigating the associated user account to understand whether information is being manipulated for malicious purposes or not.
When businesses have more information, they have more visibility. This in turn results in better and more informed decisions when managing the devices within their ecosystem and the user accounts on their app.
Mobile App Security: Key Takeaways
- Mobile apps are complex ecosystems and fraud can happen at multiple checkpoints
- Understanding which malicious tools are used to commit fraud is vital for mobile app security
- Strong device fingerprinting is key to fighting fraud
When it comes to fraud prevention, every company is different and no one size fits all. For example, some businesses are more accommodating to certain malicious tools and fraud types, such as gaming companies and emulators, or streaming services and account sharing. Other businesses are more forgiving of bots, as they can boost uptake and increase brand visibility.
But what all businesses must do, no matter their size, shape, or scope, is sit down with their various stakeholders and departments, from engineering and fraud to payments and marketing, and decide on their strategy for growth and fraud prevention. Once these have been decided, they must implement a solution that can accurately and persistently identify every device within their ecosystem, so that they can continue providing their good users with the safest and most trusted online experience.


 1. App Cloners
1. App Cloners 2. VPN Apps
2. VPN Apps 3. GPS Spoofers
3. GPS Spoofers